If you have a Synology with the running LDAP Application you can use this to have a central user management. This will allow dedicated users to login into your Firewall or their services (VPN).
First you have to download and install the LDAP package on your Synology and make sure that you have a fix IP Adress in your LAN.
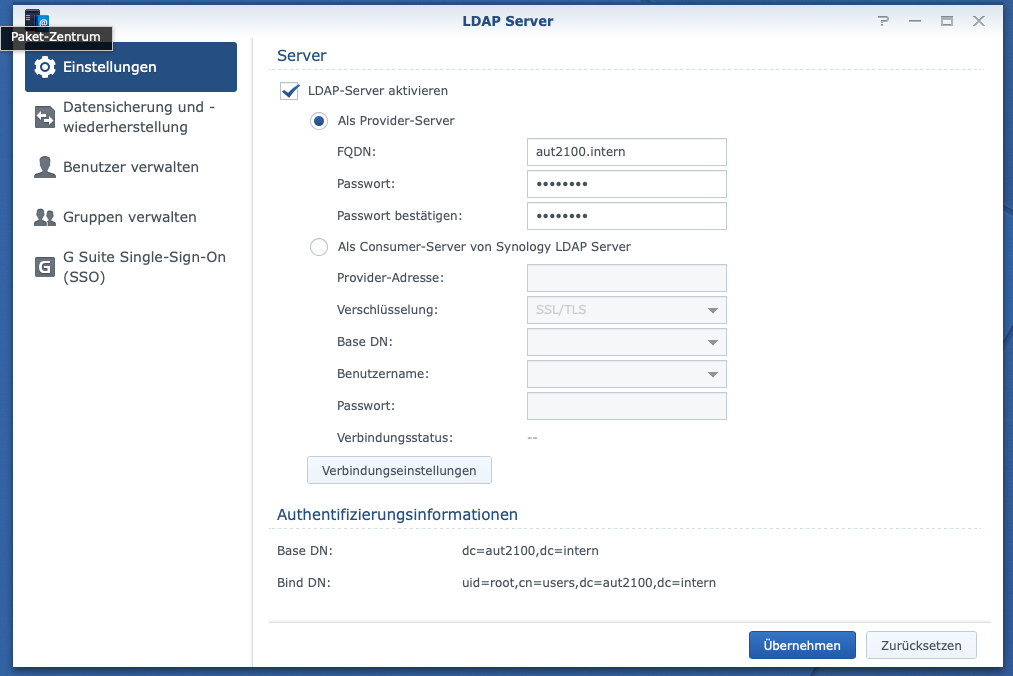
You have to set your FQDN (Fully-Qualified Domain Name) and your directory password. Now you can create users and groups. I would recommend that you create a group for users you want to allow services on your firewall for example vpn services. I use the group „vpnallow“ and add the user who I want to have access to my VPN services.
Login to your firewall and go to the settings tab, Object and then AAA Server

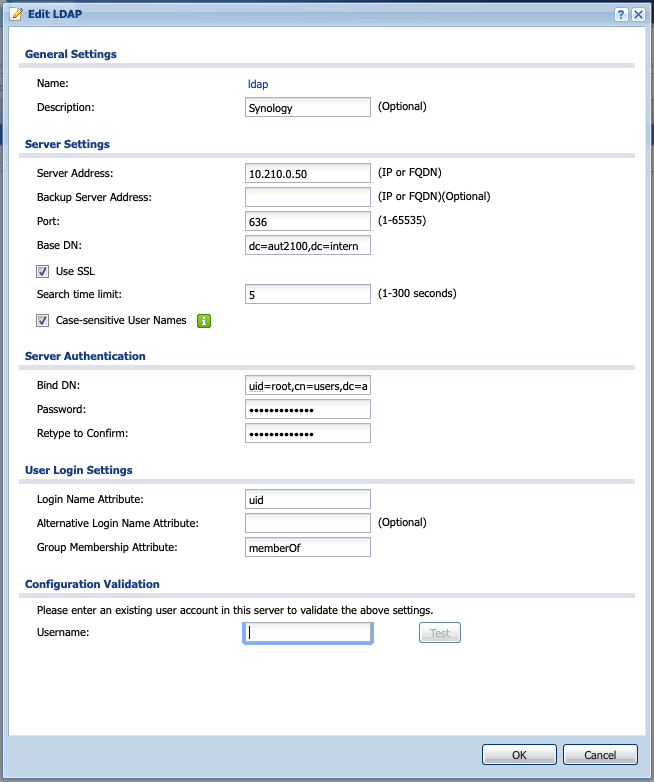
Go to LDAP and now you can use the „Add“ Button to get into the configuration.
Server Address: is the IP of your Synology, if you have done a correct DNS configuration in your local network you can use the FQDN.
Port 636: if you use SSL what I would recommend, you have to change the Port and check the checkbox „Use SSL“
Base DN: is the same what you find in the Synology LDAP application on your Synology in the Settings tab. In my example it is dc=aut2100,dc=intern
Bind DN: you can find this on the Synology LDAP application too. For example uid=root,cn=users,dc=aut2100,dc=intern. Use the password you have typed in when creating the LDAP.
Login Name Attribute: you can leave it like it is: uid
Group Membership Attribute: change it to “memberOf„ this will describe the attribute what is used to identify the group
Now you can test your configuration by typing the username in the last field and press „Test“.(You have to use an user which is member of the group you want to add) If everything is correct you should get „OK“ as Test Status. Important for us is the Returned User Attributes:
dn: uid=XXX,cn=users,dc=aut2100,dc=intern
objectClass: top
objectClass: posixAccount
objectClass: shadowAccount
objectClass: person
objectClass: organizationalPerson
objectClass: inetOrgPerson
objectClass: apple-user
objectClass: sambaSamAccount
objectClass: sambaIdmapEntry
objectClass: extensibleObject
cn: XXXX
uid: XXXX
gecos: XXX XXX
uidNumber: 1000004
gidNumber: 1000001
loginShell: /bin/sh
homeDirectory: /home/XXX
shadowLastChange: 18352
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
shadowExpire: -1
shadowInactive: 0
shadowFlag: 0
sn: XXXX
mail: XXXX@XXXX.XXX
authAuthority: ;basic;
apple-generateduid: XXXXX-53FB-4F2B-BCCA-F0330E7166A7
sambaSID: S-1-5-21-XXXXXX-613372285-2155760070-1019
sambaNTPassword: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
sambaLMPassword: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
sambaPasswordHistory: 0000000000000000000000000000000000000000000000000000000000000000
sambaPwdLastSet: 1585651462
sambaAcctFlags: [U ]
displayName: XXXXX
userPassword:: XXXXXXXX
memberOf: cn=vpnallow,cn=groups,dc=aut2100,dc=intern
memberOf: cn=2100,cn=groups,dc=aut2100,dc=intern
memberOf: cn=Familie,cn=groups,dc=aut2100,dc=intern
memberOf: cn=vds,cn=groups,dc=aut2100,dc=intern
memberOf: cn=users,cn=groups,dc=aut2100,dc=intern
Copy the text after „memberOf:“ with the group you want to add later for example: „cn=vpnallow,cn=groups,dc=aut2100,dc=intern“
Creating allowed User:
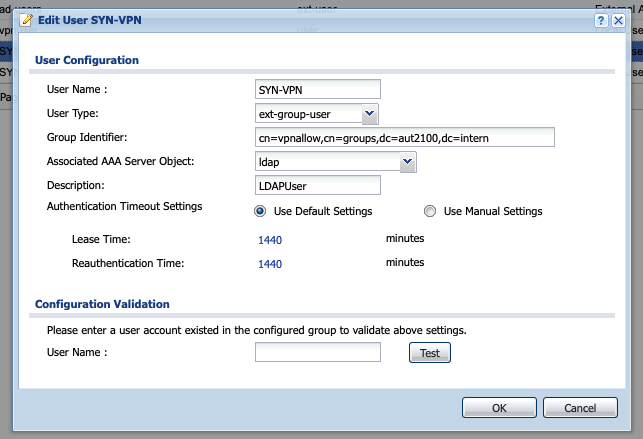
Go to Objects -> User/Groups and press on the „Add“ Button. Choose „ext-group-user“ and give in the copied string for example: „cn=vpnallow,cn=groups,dc=aut2100,dc=intern“. Change „Associated AAA Server Object:“ to ldap. Now you can test if the user is member of the group or not.
Add to Authentication Method
Go to Objects -> Auth. Method and press on the „Add“ Button. Name your new Authentication Method and press on the „Add“ Button. Choose the name you gave the LDAP / AAA Server.
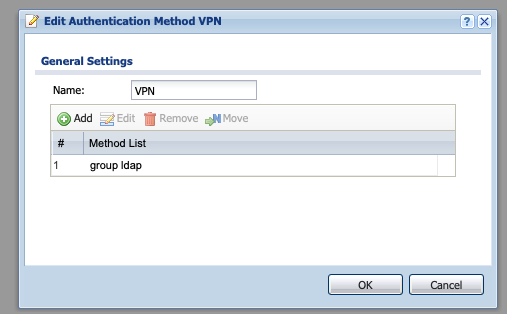
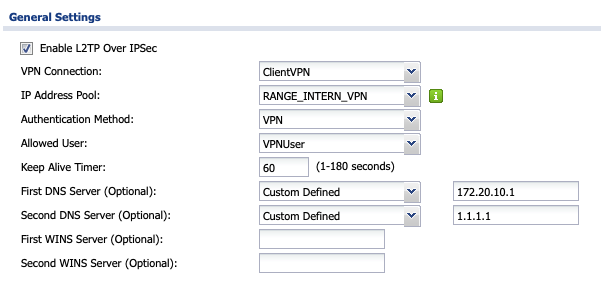
Enable the User in the VPN Settings
Now you can choose the Authentication Method you have added before and choose the Allowed User you have created.
Thanks to Tools at Work
If you have any questions or if you need help installing your firewall call them
